Authy OneTouch – Modern Authentication For Any Application

Authy this week has moved the needle forward in regards to providing better security for users, and the applications they use online. We have announced the public release of OneTouch, a new security feature in Authy that allows developers to integrate stronger security capabilities into their applications. OneTouch can be used to protect user logins and high-value transactions, such as money transfers, mass data changes, or in-game trading. Reliable authentication is delivered via easy-to-respond, real-time push notifications that minimize friction associated with traditional security technology by maximizing the user experience.
 Strong Security Technology
Strong Security Technology
Data breaches and online attacks have become a common occurrence, and applications that rely on passwords, PINs, security questions, or other knowledge-based methods of authentication are more vulnerable to online attacks like social engineering. Strong security technology like two-factor authentication has already improved upon the weakness of the password through one-time codes that can be sent through SMS, but the new OneTouch makes authentication even more user-friendly while actually increasing security.
OneTouch uses the same mobile device push notification technology that informs you about calendar reminders, social media activity, or nearly any other mobile service and combines it with standardized public/private key encryption hosted via a simple and modern web-based API. By using push notifications, OneTouch displays more information during the authentication, aiding the user in the decision-making process.
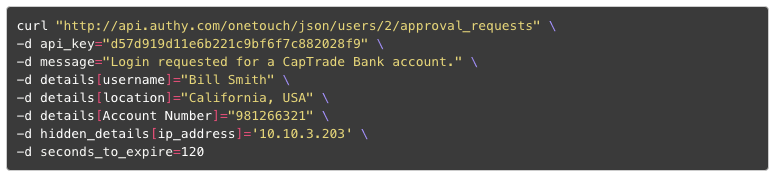
With SMS-based authentication, end users simply get a token. If the activity is fraudulent, the token is the only indication of someone trying to access your account. OneTouch allows application developers to customize the communication: What device is the request made from? From what location? What is being accessed? This information gives users confidence in approving or deny login requests. When a request is denied, this same information is audited and allows the owner of the application to lock down accounts and investigate attacks against their systems.
This simplified authentication process can be implemented in place of a password. After a user has registered a device, subsequent user authentications to your service are as simple as providing a username and responding to an Authy OneTouch notification. It is like Yahoo’s Account Key, except there’s no need to invest time and resources into building this solution yourself, OneTouch comes in an easy-to-implement API that you can have you up and running in just a short time.
Not Just About Authenticating The Login.
OneTouch is also used to implement security for any sensitive transactions that take place in your application which require timely human approval: financial transactions, changes to employee information in HR systems, sensitive application configuration change, or massive website modifications (e.g. deleting a lot of users). As an example, an Authy customer BitWage uses our 2FA service for the protection of BitCoin-based payroll and they implemented OneTouch for multi-party authentication. Their service often requires secure approval from multiple people to authorize transactions, and push notifications are a far more satisfactory experience than emails, phone calls or having to repeatedly input password credentials.
Authy OneTouch is delivered with industry standard public/private key encryption, and implements device security methods such as Apple Touch ID. Authy security technology is already used by companies like Cloudflare, Dell and Coinbase to secure accounts for their millions of customers.
Authy helps us protect our users when they access their accounts. We are excited about the ease of use OneTouch brings and we can’t wait to deploy it
Brian Armstrong, Founder and CEO of Coinbase
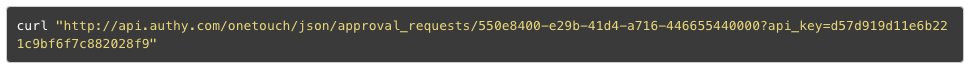
How easy is it to implement OneTouch? The notification and approval process is delivered through two simple RESTful API calls. First you create an approval request, passing in your custom message. This returns to you a unique (uuid) identifier for that request.
Then, there are two methods to process the user’s response. Either you give Authy a URL, to which we send data about a users response, that your application then processes. Or you can poll Authy asking for a status update for the specific approval request.
These two API calls are inserted in your application logic that handles the event you are protecting. To start building or prototyping today, simply sign up for an account or login to your existing Authy dashboard to enable OneTouch for your application.