What Heartbleed Means for 2FA
 Last Monday, Heartbleed, which is perhaps the worst vulnerability in recent history, was disclosed. The vulnerability was present in OpenSSL for 2 years (since March 2012) and it was discovered by two independent security researchers at the same time, so it’s very likely that it was already known and exploited by other parties for a long time.
Last Monday, Heartbleed, which is perhaps the worst vulnerability in recent history, was disclosed. The vulnerability was present in OpenSSL for 2 years (since March 2012) and it was discovered by two independent security researchers at the same time, so it’s very likely that it was already known and exploited by other parties for a long time.
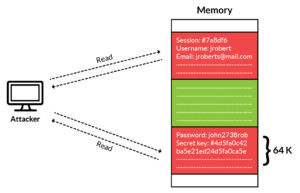
Technically speaking, the bug allows anyone to remotely read 64 kilobytes of memory at a time from a remote server. The data is whatever the server has on memory at the time, which is mostly what’s being encrypted/decrypted on the SSL/TLS channel – passwords, session ids, ssl keys, private information, etc. So imagine being able to read very sensitive information from any server in 64K intervals for as long as you like. That’s how serious this issue is.
So what does this mean for Two-Factor Authentication? Let’s start with the good and then go to the bad.
The good
Many passwords were disclosed (in plain text). If you had Two-Factor Authentication it means your accounts might still be safe. Because the most common form of Two-Factor Authentication uses time/counter based One Time Password (OTP) tokens, if any OTP was disclosed, it would be useless because it would already be either used or expired.
Why do we say might? Because it’s possible and likely that the secret seed that generates the OTP tokens could also have been disclosed. Still, the odds are in your favor if you using Two-Factor Authentication. So if you aren’t using it, let this event be a reminder that you should enable it for your all accounts now.
The bad
The most common form of Two-Factor Authentication is TOTP. TOTP uses a secret seed and the current time to generate each of the individual authentication tokens. Essentially:

Given that anyone can know the current time, if the attacker knows the secret seed, he can essentially generate a valid OTP token at any time.
So it’s possible that the secret seed that you are using for Two-Factor Authentication might be compromised.
What this means for services using Authy
Before We go in-depth, We want to make sure you know that if you are using sites with Two-Factor Authentication powered by Authy, all your seeds were rotated and you are safe.
Let me explain how we did this so fast. When we designed Authy, we built a key revocation protocol on top of TOTP. We didn’t do this to protect ourselves from this type of vulnerabilities, we built it because we were concerned that our own servers could be hacked (just as RSA Security was hacked). This feature also allowed us to revoke and seamlessly exchange all of Authy secret seeds.
How does this protocol work? Whenever you are registering your smartphone with Authy, along with the secret seed, we also generate a new RSA key-pair. We send the private key to your smartphone (without ever touching disk) and then store the corresponding public key on our servers.
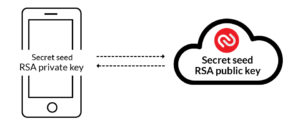
So essentially your smartphone has a secret seed for each account plus an RSA private key. The RSA private key is never stored on our servers at any time.
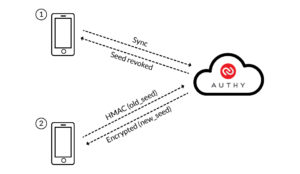
To re-issue new secret seeds, we revoke the current ones on our servers and then generate new ones. Now the interesting part is how we securely send these new keys seamlessly to your smartphone. When you start the Authy App, your phone contacts our API, which informs the phone that your secret seeds have been revoked. Your phone then sends proof to Authy that it has the revoked keys (which the attacker might have), and the private RSA key (*which only you have). Once the server verifies that you are in possession of both, it encrypts the new seeds with the corresponding public RSA key and sends them back. Since only your phone has the private RSA key, only you can decrypt the new seeds for your account.
We began rotating keys yesterday. If you are an Authy user, all you need to do is open the App and wait for a few seconds and the keys will be rotated. Also note that you don’t have to sync right away to be safe, all keys have already been revoked on our servers and are no longer valid. This also means that if you are traveling, your tokens might stop working unless you are connected to the Internet. If this happens, just connect to any Wifi network and the app will correctly sync.
*There is still a small chance (though very low) that both your RSA private key and seeds where disclosed. If you are worried about this, reinstalling the App will re-issue both
What it means for other services, e.g.: Authenticator.
Given the severity of the issue, it is very important that you rotate all of your Two-Factor Authentication seeds.
However, to do this for sites which aren’t powered by Authy’s Two Factor Authentication, you’ll have to manually go through each of the websites for which you have an Authenticator token, revoke the current secret seed and then generate a new one. Unfortunately, not all sites allow you to do this, so you might have to contact them to find out how to revoke your current secret seed.
If you are a site administrator, we encourage you to revoke the current seeds and request users re-enroll their Two-Factor Authentication on their next login.
Summary
This bug is a perfect reminder of why practicing defense in-depth works. When things go badly in one place, you can rely on your other systems to mitigate and quickly recover from the damage.
We are glad we architected our system to recover from hack attacks. Thanks to this we were able to quickly revoke more than 1 million secret seeds and securely exchange them without disruption or end-user intervention. For all Authy powered tokens, users will simply open the app and it will automatically sync the new secret seeds – no further action is required. In fact they will probably not even notice anything happened.
Heads Up for Developers
If you are a developer and you manage a website or web application, this is a reminder that you should urgently offer Two-Factor Authentication to your users. Check out Authy if you’re looking for a service you can trust to offer a secure, convenient and seamless Two-Factor Authentication experience for your users.